Security and Windows 7
It’s been a tough decade for Windows users. As Microsoft’s operating system entered the dominant phase of its existence, hackers began focusing almost solely on Windows, as that’s where all the users are. As a result, various Windows versions have suffered through a seemingly never-ending series of electronic attacks, security vulnerabilities, and high-profile malware breakouts.
In 2003 Microsoft halted development of its major operating system and application products and began an internal review of its software-development practices. The company reexamined the source code to its then-current projects and developed a new softwareengineering approach that is security-centric. Now the software giant will not release any software product that hasn’t undergone a stringent series of security checks. Windows Vista was the first client operating system shipped that was developed from the get-go with these principles in mind. That is, it was architected to be secure from the beginning. Windows 7 continues this trend quite nicely and builds off the work begun in Windows Vista.
Is Windows 7 impenetrable? Of course not. No software is perfect; but Windows 7 is demonstrably more secure than its predecessors. And although Windows users will no doubt face awesome security threats in the future, Microsoft at least has the lessons it learned from the mistakes of the past to fall back on. Many people believe that the security enhancements in Windows 7 will prove to be a major reason many users will upgrade to this version. This is completely valid.
Windows 7’s security features permeate the system, from top to bottom, from the highprofile applications, applets, and control panels you deal with every day to the low-level features most Windows users have never heard of. This chapter highlights most of the Windows 7 security features that affect the user experience, starting with those you will likely have to deal with as soon as you begin using Microsoft’s latest operating system. First, however, take a look at the first thing Windows 7 users need to do to thoroughly secure their system.
Securing Windows 7 in Just Two Steps
Out of the box, Windows 7 includes antispyware functionality in the form of Windows Defender, a two-way firewall in Windows Firewall; a hardened Web browser (Internet Explorer 8); and automatic updating features that keep the system up-to-date, every day, with the latest security patches. Also included are changes to the User Account Control (UAC) feature, covered in the next chapter, making it less annoying and less likely to be turned off, thus reducing your exposure to malware. It would seem that Windows 7 comes with everything you need to be secure.
Sadly, that’s not quite the case. First, Microsoft makes it too easy for users to opt out of one of the most important security features available in the system. In addition, one glaring security feature is missing from Windows 7. You’ll want to make sure you correct both of these issues before using Windows 7 online. Fortunately, doing so takes just two steps:
1. Enable automatic updating:
If you set up Windows 7 yourself, one of the final Setup steps is configuration of Automatic Updates, the Windows Update feature
that helps to ensure your system is always up-to-date. However, Automatic Updates can’t do its thing if you disable it, so make sure at the very least that you’ve configured this feature to install updates automatically. (Optionally, you can enable the installation of recommended updates as well, but these are rarely security oriented.) We can’t stress this enough: this feature needs to be enabled. If you’re not sure how it is configured, run Windows Update (Start Menu Search and then type windows update) and click Change Settings in the left side of the window. Make sure the option under Important updates Install updates automatically(recommended) is selected.
2. Install an antivirus solution:
Many new PCs are preinstalled with security suites from companies such as McAfee and Symantec. While these suites are better than
nothing, they’re also a bit bloated and perform poorly in our own tests. We prefer standalone antivirus solutions for this reason. There are many excellent options, including ESET NOD32 Antivirus, which in our own tests has proven to do an excellent job with minimal system impact. You can find out more about ESET NOD32 Antivirus from ESET directly. Security in Windows 7 starts with this simple rule: leave all the security settings on, at their defaults, and install an antivirus solution. That said, a full understanding of what’s available in Windows 7 from a security standpoint is, of course, beneficial. That’s what this chapter is all about.
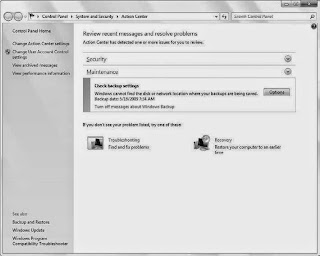
Action Center
When Microsoft shipped Windows XP Service Pack 2 (SP2) in the wake of its 2003 security- code review, one of the major and obvious new features it added to the operating system was the Security Center, a dashboard or front end of sorts to many of the system’s security features. In Windows XP SP2, the Security Center was designed to track the system’s firewall, virus protection, and Automatic Updates features to ensure that each was enabled and as current as possible. If any of these features were disabled or out-ofdate,the Security Center would warn the user via a shield icon in the notification area near the system clock, or via pop-up warning balloons.
Security Center continued in Windows Vista and picked up even more security monitoring duties. But in Windows 7, the Security Center has been rebranded and dramatically updated to support new security features, house common tasks, and provide notifications in a less intrusive way. Windows 7’s Action Center is barely recognizable as the successor to the XP and Vista Security Center. There’s actually a lot more going on there once you begin examining its new functionality.
The core behavior of this tool hasn’t changed in Action Center. The Action Center still tracks certain security features and ensures that they’re enabled and up-to-date. If they’re not, the Action Center subtly notifies you by changing its notification area flag icon (using a small red “x” icon overlay), instead of irritating you with a pop-up balloon as before. As noted previously, Action Center now tracks far more items. Here’s the list:
♦♦ Security Features
- Network firewall: The Action Center ensures that Windows Firewall (or a third-party firewall) is enabled and protecting your PC against malicious software that might travel to your PC via a network or the Internet.
- Windows Update: Like Windows XP and Vista, Windows 7 includes an Automatic Updates feature that can automatically download and install critical security fixes from Microsoft the moment they are released. Action Center ensures that Automatic Updates is enabled.
- Virus protection: Although Windows 7 doesn’t ship with any antivirus protection, Action Center still checks to ensure that an antivirus service is installed and up-to-date. Modern antivirus solutions are designed to integrate with Windows Action Center so that the system can perform this monitoring function.
- Spyware and unwanted software (malware) protection: Windows 7, like Vista, ships with Windows Defender, the malware protection suite. Action Center will monitor Windows Defender (or your anti-spyware solution of choice) and ensure it’s running and using the latest definitions.
- Internet security settings: The Action Center ensures that Internet Explorer 8 is configured in a secure manner. If you change any IE security settings Action Center will warn you about this issue.
- User Account Control: The Action Center also ensures that the User Account Control (UAC) technology is active. This tool is described in Chapter 8.
- Network Access Protection: Network Access Protection, first broadly provided with Windows Server 2008, enables IT administrators to protect the security of a network by ensuring that connected PCs (running Windows XP, Vista, or 7) pass software and settings checks, created by the administrator. These checks, for example, can reveal a required piece of corporate software or ensure that certain network authentication settings are configured properly. Any deviations from this configuration will be picked up and passed on to you by the Action Center.
♦♦ Maintenance Features
- Windows Backup: The Action Center takes note of whether or not you’re performing backups of your crucial data.
- Windows Troubleshooting: The Windows Troubleshooting platform in Windows 7 ties directly into the new Action Center. Action Center will alert you to any problems that should be sent to Microsoft for further analysis and any solutions that were found to solve existing issues.
- Problem reports: If you run into a software issue, Windows 7 can automatically report the problem to Microsoft and check whether a resolution is provided. Action Center monitors this feature to see whether it is enabled.If all of the features that the Action Center is monitoring are enabled and up-to-date, you won’t ever see this feature unless you manually navigate to it. (You can find the Action Center in Control Panel ➪ System and Security ➪ Action Center, or by typing action center in Start Menu Search.) However, if one or more of these features are disabled,misconfigured, or out-of-date, the Action Center will provide the aforementioned alerts. It also displays its displeasure with red prefixed sections in the main Action Center window. In such a case, you can usually resolve the issue by simply using the button provided. For example, if you don’t install antivirus software, in Action Center you’ll see a Virus protection alert along with a “Find a program online” button. After installation of the antivirus software, this alert will disappear.
If you install Windows 7 yourself, you will see a red Action Center icon in the notification area of the taskbar. This is because Windows 7 doesn’t ship with any antivirus solution: To make this warning disappear, install a third-party antivirus solution.
Windows Firewall
When Microsoft first shipped Windows XP in 2001, it included a feature called Internet Connection Firewall (ICF) that could have potentially thwarted many of the electronic attacks that ultimately crippled that system over the ensuing several years. There was just one problem: ICF was disabled by default and enabling and configuring it correctly required a master’s degree in rocket science (or at least in computer security). Microsoft wised up and shipped an improved ICF version, renamed as Windows Firewall, with Windows XP SP2. Best of all, it was enabled by default. Sure, it broke many applications at first, but now, years later, virtually all Windows applications know how to live in a firewall-based world.
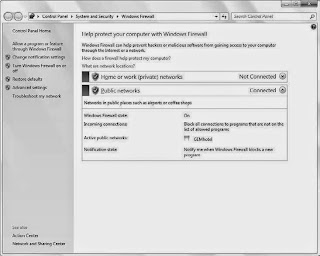
In Windows Vista, we were given an even better version of Windows Firewall. Unlike the XP SP2 version, the version in Windows Vista enabled monitoring both outbound and inbound network traffic. While Windows 7 doesn’t bring many Windows Firewall additions, it does feature a much more informative interface, as shown in Figure.
Windows Firewall is initially configured to block any unknown or untrusted connections to the PC that originate over the network. You can enable exceptions to this behavior via the Allowed Programs list, which you can access by clicking the link Allow a program or feature through Windows Firewall. Typically you just leave the settings as is, of course. Depending on the network type (Home, Work, or Public) chosen when Windows 7 connects to a network, some programs and features are automatically configured to communicate through the firewall,
Windows Update
With Windows 98 over a decade ago, Microsoft introduced a Web-based service called Windows Update that provided software updates to Windows users. That service has since been superseded by Microsoft Update, which also provides updates to many other Microsoft software products. In Windows Vista, Windows Update was moved into the operating system and made a client application, eliminating the number of Web browser hoops you had to jump through to keep your operating system up-to-date. Windows 7 continues
to carry the Windows Update torch, making a few subtle changes for the good.
As shown in Figure, Windows Update remains a client application that you can access from the Start menu. From here, you can check for and install new updates, hide updates you don’t want to be alerted about anymore, and view the history of updates you’ve already installed. You can also click a link to enable Microsoft Update functionality, enabling Windows Update to download and install updates for other Microsoft applications, such as Microsoft Office and various Windows Live products
Internet Explorer 8 Security Features
Internet Explorer 8 comes with Windows 7 and includes a vast number of security improvements that make this the safest version of IE yet. This section examines the security features Microsoft added to Internet Explorer 8. These features were absolutely necessary: ever since Microsoft integrated Internet Explorer with the Windows shell beginning in the mid 1990s, Internet Explorer has been a major avenue of attack against Windows.
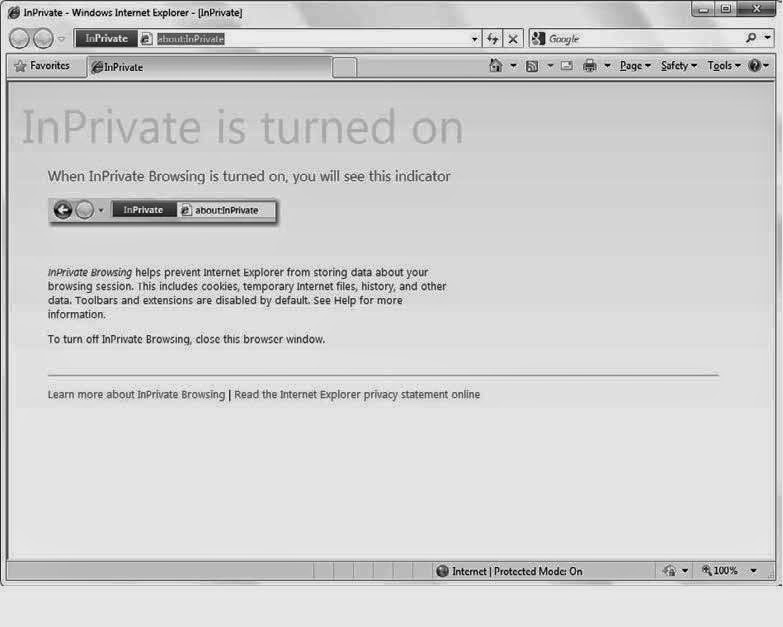
Internet Explorer 8 can optionally run in a new InPrivate Browsing mode, shown in Figure , effectively hiding your tracks as you travel around to the more nefarious parts of the Web or, what the heck, secretly shop for a spouse’s birthday present online. More specifically, InPrivate Browsing turns off IE’s ability to locally store or retain browser history, temporary Internet files, form data, cookies and user names, and passwords. It does allow you to download files and add sites to your Favorites. By default, IE add-ons like
toolbars are disabled in InPrivate Browsing mode, but you can change that from Internet Settings if desired
A related feature, InPrivate Filtering, is a first step in addressing the way in which many Web sites share data with each other. Consider a mainstream Web site like wsj.com, for The Wall Street Journal. This site is certainly reputable, but it utilizes advertising services that work across multiple non-WSJ Web sites. Once these services have collected information about you on wsj.com, they can track you across other sites that utilize the same services. This is usually innocuous, but it’s possible that a malicious site could take advantage of this capability and deliver dangerous content via other sites.
InPrivate Filtering provides basic protection against this potential kind of attack by preventing, by default, more than 10 cross-site calls. It’s not enabled by default, however, but once you enable it you have decent control over how it works. For example, you could lower the threshold for cross-site content (down to a minimum of three), choose to allow or block specific sites, and so on. It’s interesting to look at just to see what the sites you visit are up to. You might be surprised.
SmartScreen Filter
IE8’s SmartScreen Filter is the new version of the anti-phishing filter that debuted in IE7. It’s been renamed to reflect the fact that it now performs both anti-phishing and antimalware functions, protecting you and your PC from electronic attacks. So if you attempt to browse to a site that is known to deliver malware, or you attempt to download a known bad file, IE8 will prompt you with a warning.
You can manually check the current Web site if you’re unsure of something. When you do so, the SmartScreen Filter tells you what it knows about the site. You can also report a Web site that you think might be fraudulent. Microsoft says that almost 50 percent of the data in its SmartScreen database comes from users.
Should Internet Explorer 8 somehow be compromised, there’s a way out. An Internet Explorer mode called Add-ons Disabled Mode loads IE with only a minimal set of add-ons so you can scrub the system of any malicious code. You can access this mode by navigating to All Programs ➪ Accessories ➪ System Tools ➪ Internet Explorer (No Add-ons) in the Start menu. Alternately, you can use Start Menu Search to find Internet Explorer (No Add-ons).